Setup Single Sign-On via Okta
This page guides you through setting up Okta for Single Sign-On with Airbyte.
Airbyte will communicate with your Okta account using OpenID Connect (OIDC).
Creating an Okta app for Airbyte
The following steps need to be executed by an administrator of your company's Okta account.
You will need to create a new Okta OIDC App Integration for your Airbyte. Documentation on how to do this in Okta can be found here.
You should create an app integration with OIDC - OpenID Connect as the sign-in method and Web Application as the application type:
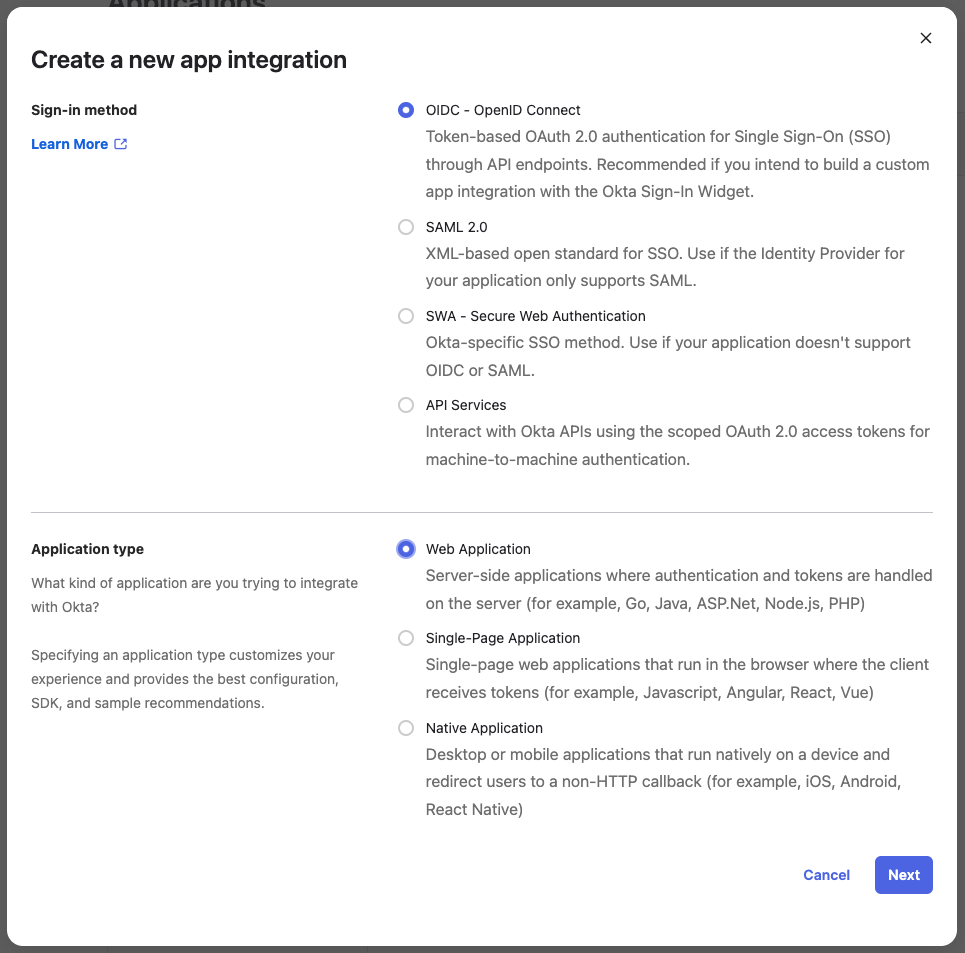
On the following screen you'll need to configure all parameters for your Okta application:
- Cloud
- Self Hosted
You'll require to know your Company Identifier to fill in those values. You receive this from your contact at Airbyte.
Create the application with the following parameters:
- App integration name
- A human readable name for the application (e.g. Airbyte Cloud). This is only used for identification inside your Okta dashboard.
- Logo (optional)
- You can upload an Airbyte logo, which you can find at https://airbyte.com/company/press
- Grant type
- Only Authorization Code should be selected
- Sign-in redirect URIs
https://cloud.airbyte.com/auth/realms/<your-company-identifier>/broker/default/endpoint- Sign-out redirect URIs
https://cloud.airbyte.com/auth/realms/<your-company-identifier>/broker/default/endpoint/logout_response- Trusted Origins
- Leave empty
- Assignments > Controlled Access
- You can control whether everyone in your Okta organization should be able to access Airbyte using their Okta account or limit it only to a subset of your users by selecting specific groups who should get access.
You'll need to pass your Airbyte contact the following information of the created application. After that we'll setup SSO for you and let you know once it's ready.
- Your Okta domain (it's not specific to this application, see Find your Okta domain)
- Client ID
- Client Secret
- Email Domain (users signing in from this domain will be required to sign in via SSO)
For security purposes, existing Applications used to access the Airbyte API that were created before enabling SSO will be disabled once the user that owns the Application signs in via SSO for the first time. After enabling SSO, please make sure to replace any Application secrets that were previously in use.
Create the application with the following parameters:
- App integration name
- Please choose a URL-friendly app integration name without spaces or special characters, such as
my-airbyte-app. Screenshot of Okta app integration name Spaces or special characters in this field could result in invalid redirect URIs. - Logo (optional)
- You can upload an Airbyte logo, which you can find at https://airbyte.com/company/press
- Grant type
- Only Authorization Code should be selected
- Sign-in redirect URIs
<your-airbyte-domain>/auth/realms/airbyte/broker/<app-integration-name>/endpoint<your-airbyte-domain>refers to the domain you access your Airbyte instance at, e.g.https://airbyte.internal.mycompany.com<app-integration-name>refers to the value you entered in the App integration name field- Sign-out redirect URIs
<your-airbyte-domain>/auth/realms/airbyte/broker/<app-integration-name>/endpoint/logout_response- Trusted Origins
- Leave empty
- Assignments > Controlled Access
- You can control whether everyone in your Okta organization should be able to access Airbyte using their Okta account or limit it only to a subset of your users by selecting specific groups who should get access.
Once your Okta app is set up, you're ready to deploy Airbyte with SSO. Take note of the following configuration values, as you will need them to configure Airbyte to use your new Okta SSO app integration:
- Okta domain (How to find your Okta domain)
- App Integration Name
- Client ID
- Client Secret
Visit the implementation guide for instructions on how to deploy Airbyte Enterprise using kubernetes, kubectl and helm.